SSH Wiring Diagram: Secure Your Connections! Ssh port forwarding tunnels create local forward red host
If you are searching about Getting started with SSH security and configuration - IBM Developer you've came to the right place. We have 25 Pictures about Getting started with SSH security and configuration - IBM Developer like Securing Network Traffic With SSH Tunnels | Information Security Office, Ssh Wiring Diagram and also What is SSH (Secure Shell)? | SSH Academy. Here it is:
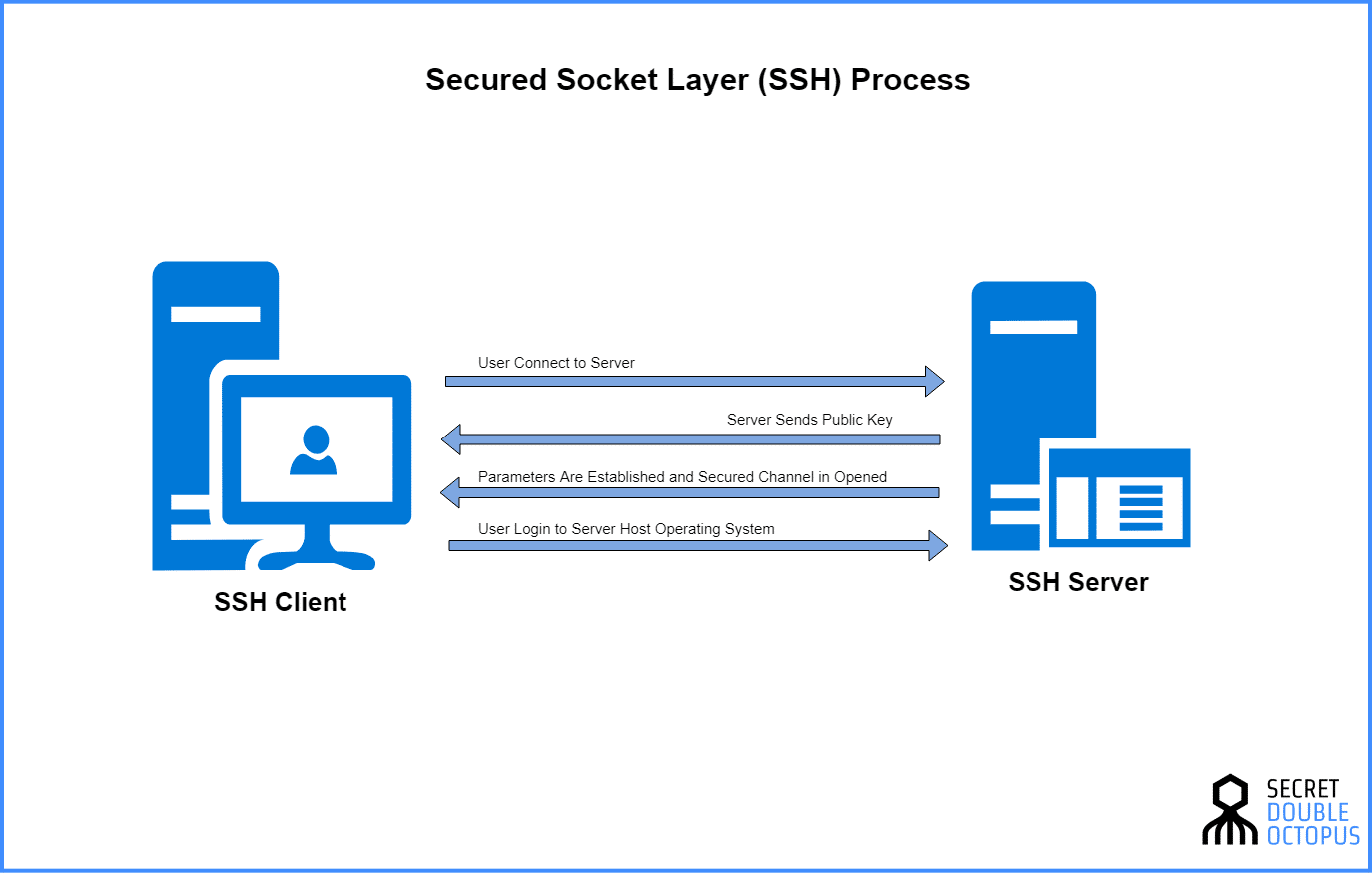
Getting Started With SSH Security And Configuration - IBM Developer
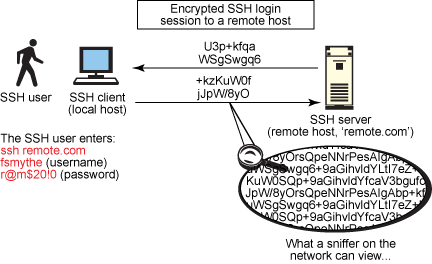 developer.ibm.com
developer.ibm.com
ssh ibm protocol developer encrypted sessions configuration
Dirk Loss: SSH Port Forwarding Visualized
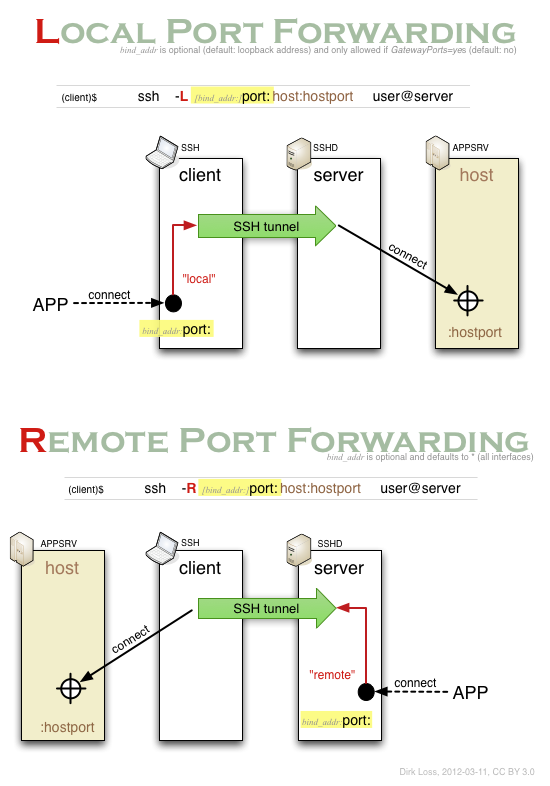 www.dirk-loss.de
www.dirk-loss.de
port forwarding ssh visualized dirk loss
Ssh Wiring Diagram
 manuallibjacoby77.s3-website-us-east-1.amazonaws.com
manuallibjacoby77.s3-website-us-east-1.amazonaws.com
RemoteIoT Web SSH Tutorial: A Beginner's Guide To Secure Shell Access
 www.passbolt.prunedge.com
www.passbolt.prunedge.com
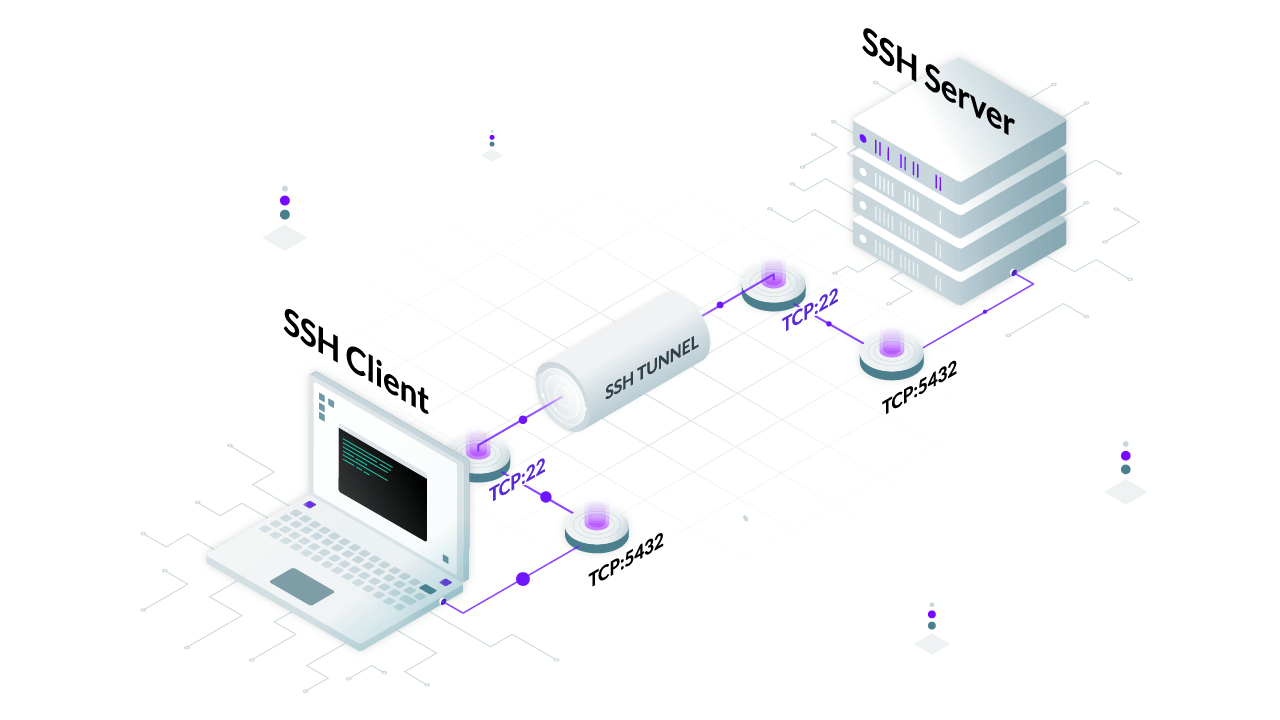
How To Create SSH Tunnels - TunnelsUP
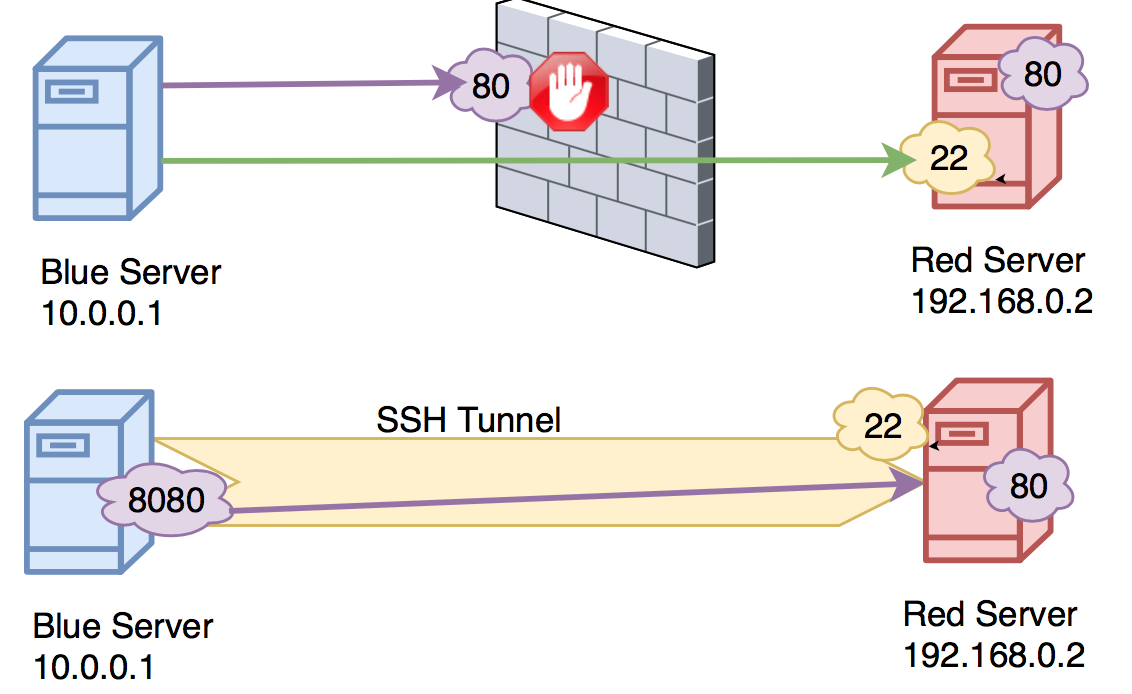 www.tunnelsup.com
www.tunnelsup.com
ssh port forwarding tunnels create local forward red host
Ssh Wiring 5 Way
What Is SSH Key?| SSH (Secure Shell) Key Management Tool - ManageEngine
 www.manageengine.com
www.manageengine.com
ssh authentication manageengine manager server
Getting Started With SSH Security And Configuration - IBM Developer
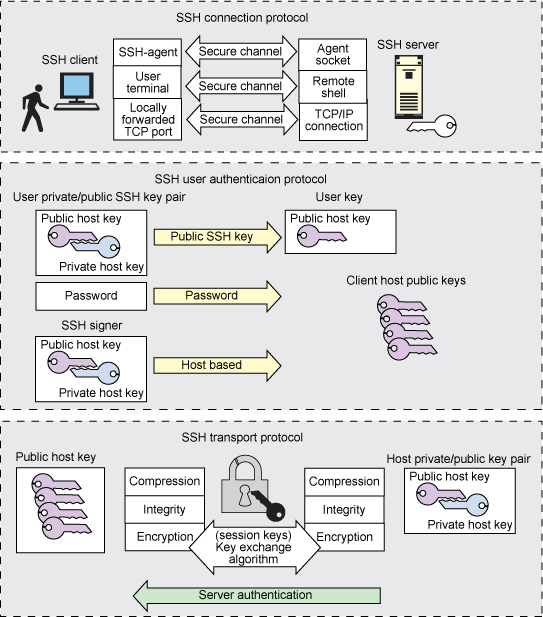 developer.ibm.com
developer.ibm.com
ssh private ibm developer pairs configuring
Securing Network Traffic With SSH Tunnels | Information Security Office
 security.berkeley.edu
security.berkeley.edu
Ssh Wiring Diagram Database
Perform Multiple SSH Hops With SSH Config And A Jump Host | LinuxServer.io
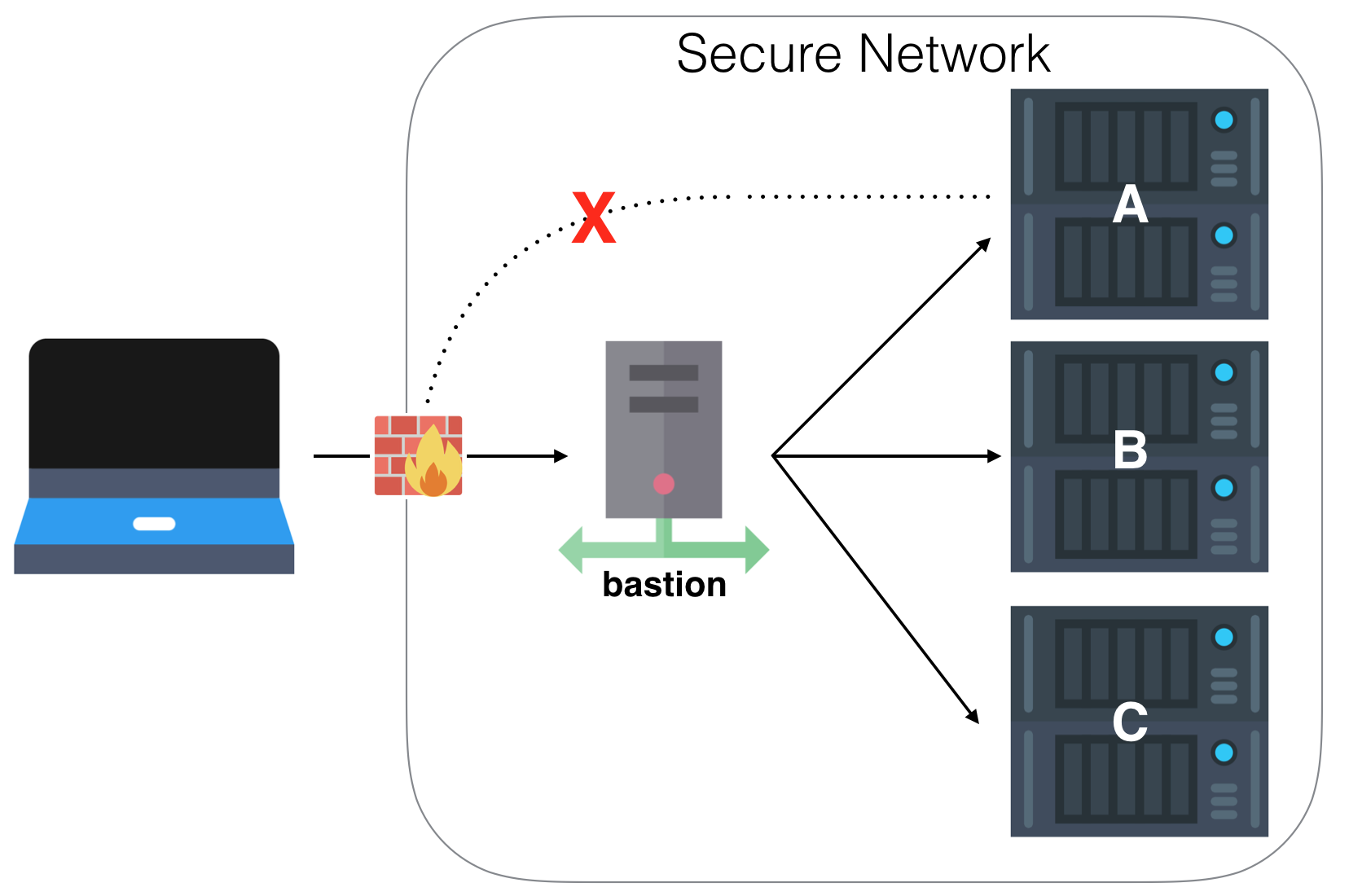 www.linuxserver.io
www.linuxserver.io
ssh jump config perform hops bastion linuxserver server
What Is SSH (Secure Shell)? | SSH Academy
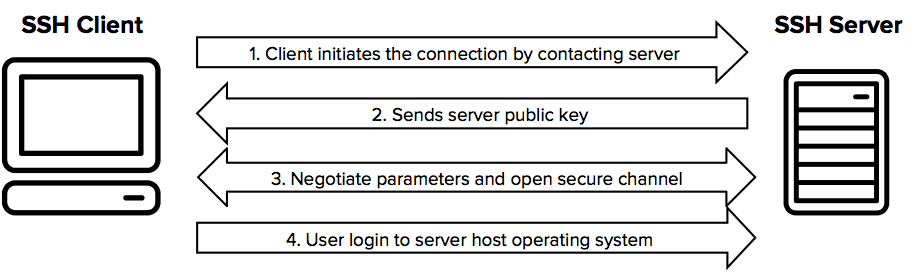 www.ssh.com
www.ssh.com
ssh protocol
Creating An SSH Reverse Tunnel
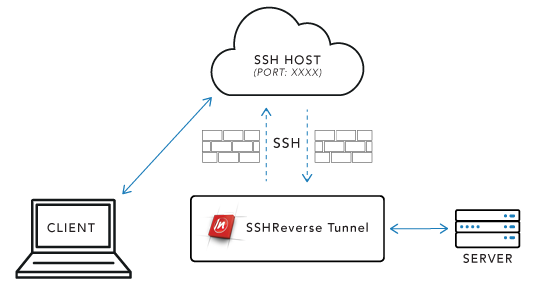 www.nsoftware.com
www.nsoftware.com
ssh reverse tunnel diagram typical scenario illustrates following
What Is SFTP (SSH File Transfer Protocol)? - IONOS CA
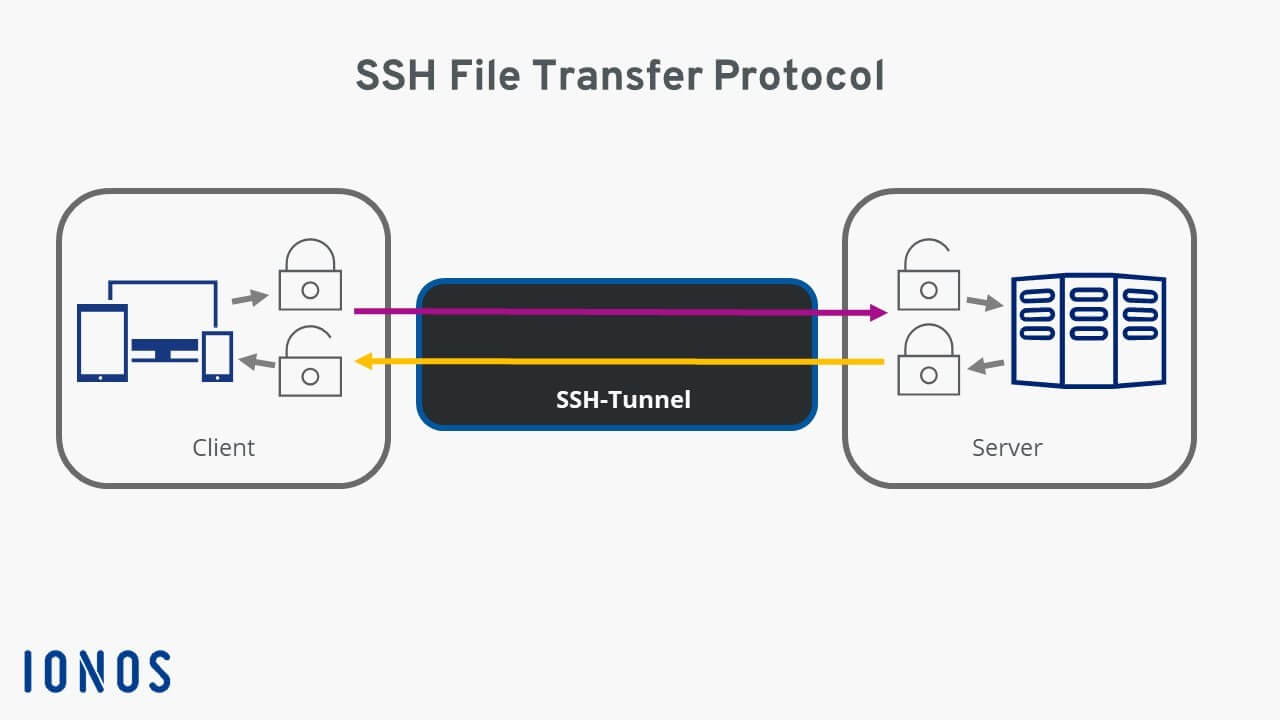 www.ionos.ca
www.ionos.ca
sftp transfer ssh file protocol data diagram secure encryption tunnel through server ionos digitalguide flows bidirectional using
What Is SSH Protocol? How Does It Work?
 www.wallarm.com
www.wallarm.com
SSH Vs. SSL: What Are The Differences?
 phoenixnap.com
phoenixnap.com
Ssh Message Flow Diagram 5: Sequence Diagram For Message Flo
 schematicverbesoleilxg2.z21.web.core.windows.net
schematicverbesoleilxg2.z21.web.core.windows.net
SSH Keys Authenticate Users And Hosts In SSH For SSO & M2M Access.
 www.ssh.com
www.ssh.com
ssh authentication protocol linux configure benefits authenticate username keygen article hosts
Ssh Wiring Diagram
 enginelibrarydaniel88.s3-website-us-east-1.amazonaws.com
enginelibrarydaniel88.s3-website-us-east-1.amazonaws.com
Understanding SSH, Telnet, And Ping
 gamma.app
gamma.app
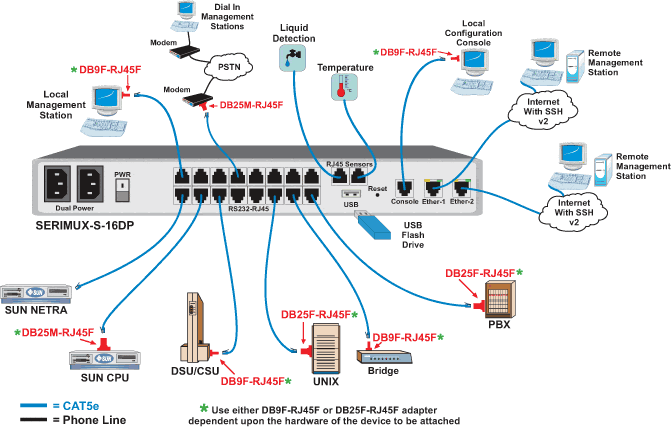
Secure SSH Serial Port Console Switch RS232 Manage Remote Server
 www.networktechinc.com
www.networktechinc.com
switch console serial cisco ssh rs232 connect connection application control port drawing via configure monitoring secure internet pc computer server
[network] What Is SSH Protocol?
![[network] what is SSH protocol?](https://velog.velcdn.com/images/soongle/post/336a7e1c-232e-4db4-b018-4ef302cfef57/image.png) velog.io
velog.io
What Is SSH Encryption And How Does It Work? | Comparitech
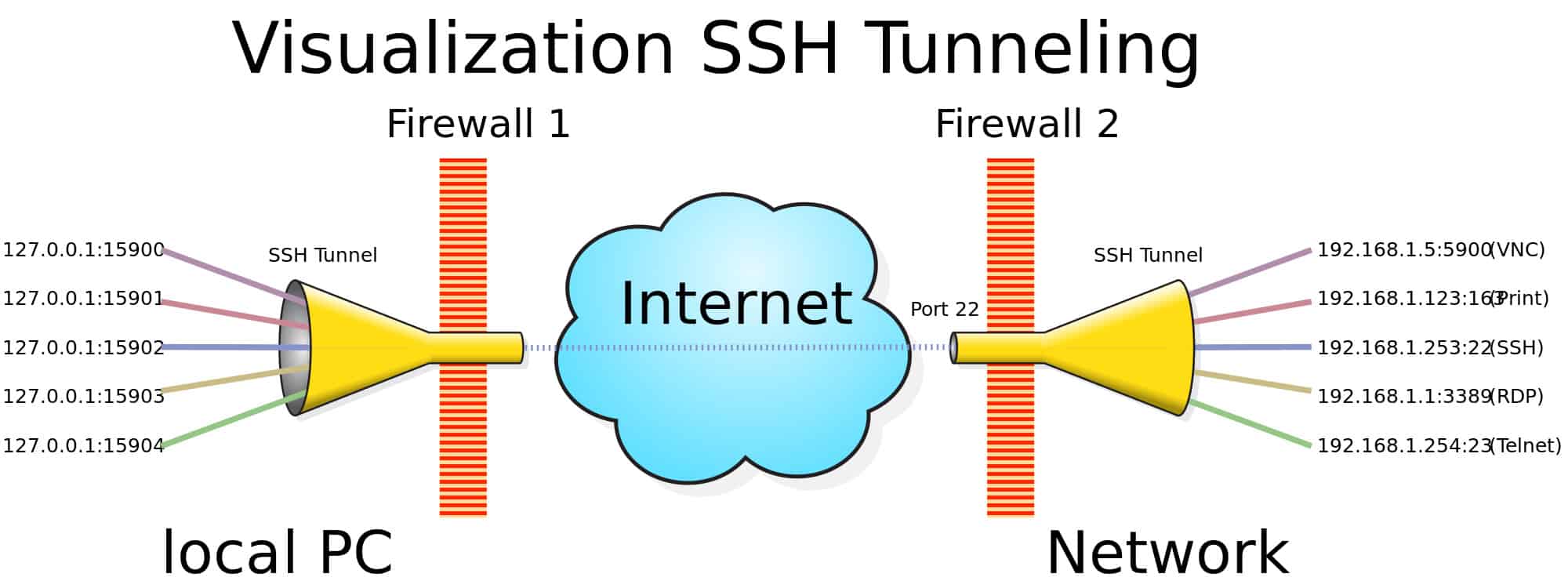 www.comparitech.com
www.comparitech.com
ssh what encryption work comparitech does tunneling computer security
What Is SSH (Secure Shell Protocol)? - H2S Media
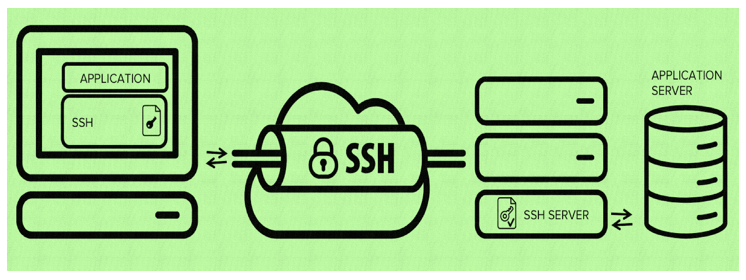 www.how2shout.com
www.how2shout.com
ssh secure protocol shell what contents show
The Complete Guide To SSH Keys In GitLab - Spectral
 spectralops.io
spectralops.io
ssh keys key gitlab private guide public server user complete any
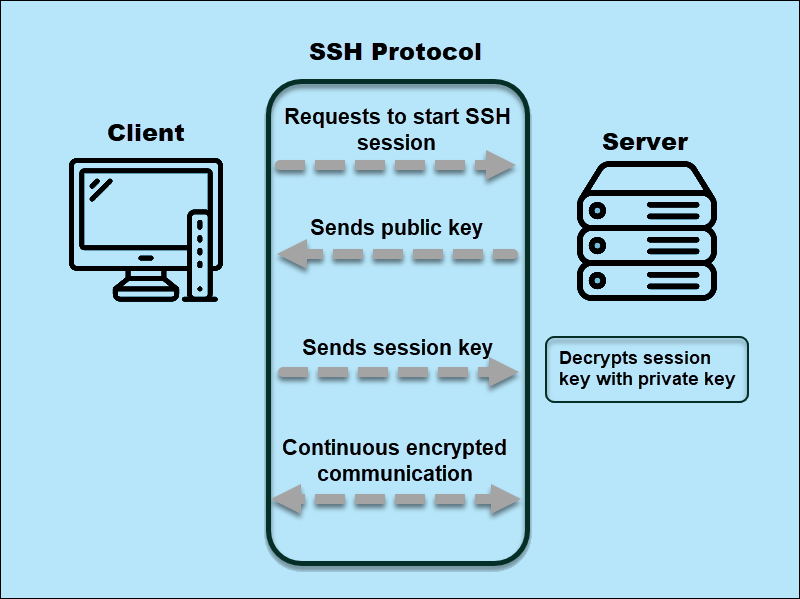
Ssh protocol. Ssh ibm protocol developer encrypted sessions configuration. Port forwarding ssh visualized dirk loss